Cryptography is the science of methods of ensuring the confidentiality and authenticity of information. Mathematical cryptography arose as the science of encrypting information, i.e. as a science of cryptosystems. In the classical model of a secret communication system, there are two participants who fully trust each other, who need to transfer information between each other that is not intended for third parties. Such information is called confidential or secret. The task of ensuring confidentiality, i.e. protecting classified information from an ill-wisher is the first task of cryptography.
The use of encryption can be traced back to 3000 BC, in the Babylonian era. Encryption technologies have evolved as they are used in military and political actions. As a result of the recent widespread use of the Internet and a sharp increase in the amount of information, people have begun to use encryption technology more often, introducing it into an increasing number of information processes, including cryptocurrency.
Ancient Times
Hieroglyphs (pictograms used in Ancient Egypt) written on a stele around 3000 BC are considered the oldest surviving example of encryption. Hieroglyphs have long been considered impossible to read, but the discovery and study of the Rosetta Stone in the 19th century was the catalyst that allowed hieroglyphs to be read.
"Script cipher" is a form of encryption used in the city state of Sparta in Ancient Greece around the 6th century BC. This involved the use of a cylinder of a certain diameter, around which a strip of parchment was wrapped, and the text was written on the strip of parchment along the long axis of the cylinder. The encryption method was designed so that the recipient could read it by wrapping parchment tape around a cylinder of the same diameter.
Encryption methods such as "scytale cipher" that rely on rearranging the sequence in which characters are read are called "transposition ciphers". The Caesar cipher, which originated in the 1st century BC, was so named because it was used frequently by Julius Caesar, and it is a particularly well-known encryption method among the many encryption methods that have emerged over the long history of encryption.
Middle Ages
Cryptography became more popular in the Middle Ages as encryption technologies became more sophisticated based on the knowledge gained from efforts to decipher classical ciphers and invent new ciphers. The increased diplomatic activity during this time led to an increase in the need for the transmission of confidential information, which led to the frequent use of encryption.
The Mary Queen Scots cipher was known as the "nomenclator cipher," and it included codes for replacing phrases in addition to replacing letters of the alphabet. These "codes" were listed in a "code book", that is, the "key" to the cipher, which was in the possession of both senders and recipients, and this made it difficult to decrypt the encryption.
Simple cipher substitutions, which include a substitution pattern for each character like the one used by Mary Queen of Scots, eventually became deciphered. Moreover, the "nomenclature" used by Mary Queen of Scots involved preparing a huge codebook and providing the codebook to every encryption user, which presented difficulties. The problem of "obtaining and providing the key" became a problem for users of advanced encryption technologies in the modern era, as well as for users in the Middle Ages.
The era of encryption machines
Around 1790, one of the founding fathers of the United States, Thomas Jefferson, created a disk cipher, later nicknamed the Jefferson cylinder. This device, based on a rotary system, made it possible to automate the encryption process and became the first crypto-device of the modern era.
The invention of the telegraph had a great influence on the encryption business. Previous ciphers suddenly stopped working, while the need for high-quality encryption only increased in connection with a series of major military conflicts. In the 19th-20th centuries, it was the military sphere that gave the main impulses for the development of cryptography. Since 1854, the British military has been using the Playfair cipher, which is based on the encryption of bigrams, or pairs of characters. This cipher was used until the outbreak of World War II.
In World War II, opponents already used mobile electromechanical encryptors, the ciphers of which were considered undetectable. The devices were rotary or on pin discs. The former included the famous Enigma machine, which was used by the Nazis, and the latter, the American M-209 machine.
The principle of operation of "Enigma" was as follows: with each press of a key with a letter of the alphabet, one or more rotors came into motion. The letter was changed several times according to the principle of the Caesar cipher. Enigma ciphers were considered the most resistant to decryption, since the number of its combinations reached 15 quadrillion. However, the Enigma code was still deciphered, first by Polish cryptographers in 1932, and then by the English scientist Alan Turing, who created a machine for decrypting Enigma messages called the Bomb. A complex of 210 such machines allowed the British to decipher up to 3 thousand Nazi military messages per day and made a great contribution to the victory of the Allies.
Little was known about Soviet encryption machines until recently information about them was classified. For example, until the 1990s, the Violet rotary encryption machine was used in the USSR and allied countries. Unlike Enigma and other devices, it used 10 rotors, and the information was displayed on paper.
Cryptography today
With the advent of computers, cryptography has become much more advanced. Stronger 128-bit mathematical encryption is now standard on many devices and computer systems. Since 1990, scientists have been developing a completely new form of cryptography, called quantum cryptography, to improve the security of modern encryption.
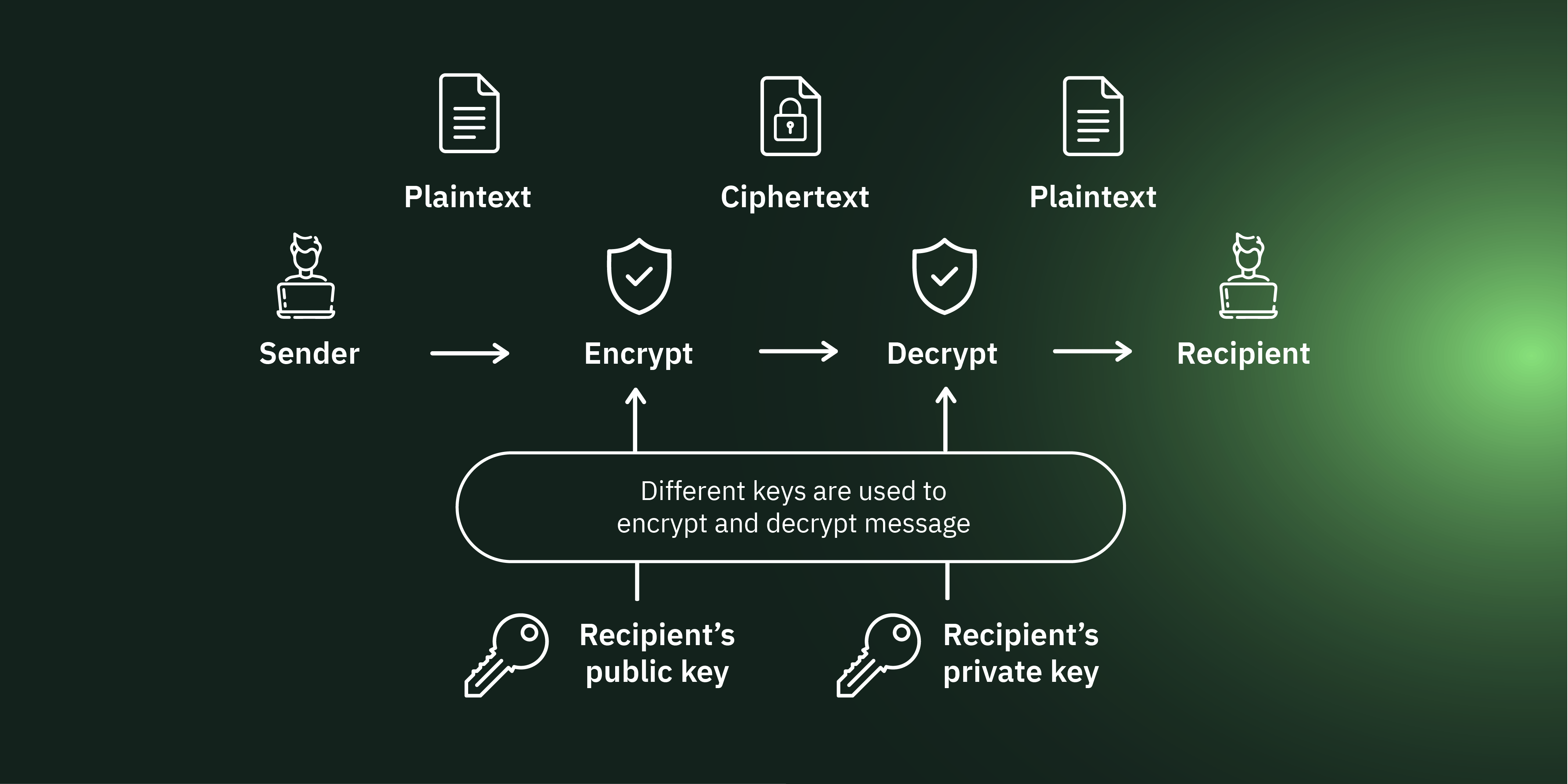
Recently, cryptographic techniques have been able to be used to create cryptocurrencies. Cryptocurrencies use several advanced cryptographic techniques, including hash functions, public-key cryptography, and digital signatures. These methods are mainly used to secure the data stored on the blockchain as well as to authenticate transactions.
Cryptography has come a long way over the past thousand years, and there are no plans to stop there. As long as sensitive data remains at risk, cryptography will continue to evolve.